Rumor Check: Those Fake Cellphone ‘Towers’ You’re Hearing About Aren’t Necessarily Towers at All
Jonathon M. Seidl
The BLAZE
A story has been taking the Internet by storm this week about an encrypted cellphone device that has uncovered 17 “fake” cell towers across America. There’s just one problem: the “towers” aren’t necessarily towers at all.
The story seems to originate from a Popular Science article last week titled, “Mysterious Phony Cell Towers Could Be Intercepting Your Calls.” It focused on how a fancy device called the CryptoPhone 500 (available for $3,500) can detect when your call has been routed through a “phony” tower. And in fact, the phone recently discovered “17 different phony cell towers known as ‘interceptors.’” The story then spread to an obscure site and beyond. But what the original article never makes clear is that the “interceptors” are not necessarily physical towers, and such devices have been known about for several years.
 A StingRay cellphone surveillance device. (Image source: U.S. Patent and Trademark Office)
A StingRay cellphone surveillance device. (Image source: U.S. Patent and Trademark Office)
In fact, TheBlaze has been reporting on interceptor devices that mimic towers since 2011, when our own Buck Sexton wrote about something known as a “Stingray” and its legality:
The Stingray is a generic term for devices that can track a cellphone’s location as long as it is turned on. As the Journal described its method of operation, the Stingray functions by:
“mimicking a cellphone tower, getting a phone to connect to it and measuring signals from the phone. It lets the stingray operator “ping,” or send a signal to, a phone and locate it as long as it is powered on.”
Law enforcement across the country does not have a standardized procedure for obtaining permission to use devices like the Stingray, though generally police agencies obtain a court order and not a search warrant, which would require a higher standard of proof.
This raises the question: should law enforcement be able to know exactly where you are without going before a judge to show probable cause?
TheBlaze TV’s Real News program continued debating the topic in February 2013 and TheBlaze has covered the Stingray numerous other times here, here, here and here. In fact, Elizabeth Kreft conducted a detailed interview this July with a security expert talking about how the Stingray (which is also a brand name in addition to the generic term) and another variation called the Hailstorm work, and why the public should know about them:
NF: These devices are pieces of physical equipment that police use themselves to track cellphones. It works by mimicking cell service providers’ cellphone towers and then sending out electronic signals that force phones — really trick phones — into reporting back their identifying information, including their electronic serial numbers and their location. A good way to describe this is that old kids pool game: so the cell site simulator will say “Marco,” and your cellphone says “Polo.”
EK: Ha. I want to laugh, but I’m too annoyed. So many ways for innocent Americans to be tracked. Now, some of these are carried and some are permanently fixed, right?
NF: One is a handheld model that is a little less powerful, others are vehicle-based that have stronger signals, some of them have directional antennas — but they all work in the same way. But there are several concerning things about how these work, much like cell tower dumps, they trigger every phone in the area — including phones of completely innocent bystanders — into reporting back their location information to the police.
This image and its caption sums it up well (don’t let the picture of the actual tower confuse you — look closely):
This graphic illustrates how a StingRay works. Signals from cellphones within the device’s radius are bounced to law enforcement. The information relayed may include names, phone numbers, locations, call records and even text messages.
This graphic illustrates how a StingRay works. Signals from cellphones within the device’s radius are bounced to law enforcement. The information relayed may include names, phone numbers, locations, call records and even text messages. (Image source: KQED)
On Thursday’s Glenn Beck Radio Program, the CEO of the company behind the CryptoPhone 500 cleared up some of the confusion: Les Goldsmith of ESD America confirmed the towers aren’t necessarily large physical structures.
“That’s the one misconception the media got from this,” Goldsmith said. ”When we say a fake cellphone tower, that can be simply a laptop with two dongles plugged into it to actually give it GSM coverage.”
“It doesn’t have to be a large fully built tower,” he added. “So you can have somebody in a hotel room with a laptop that is collecting every phone within half a mile and having it run through there instead of a normal cell tower.
“Think of it as a cellular repeater. You put a cellular repeater in your building to give you better coverage. All your calls pass through the cellular repeater. Well, an interceptor pretends to be a cell tower and passes your call on like a cellular repeater. It just turns encryption off on the way so it can listen.”
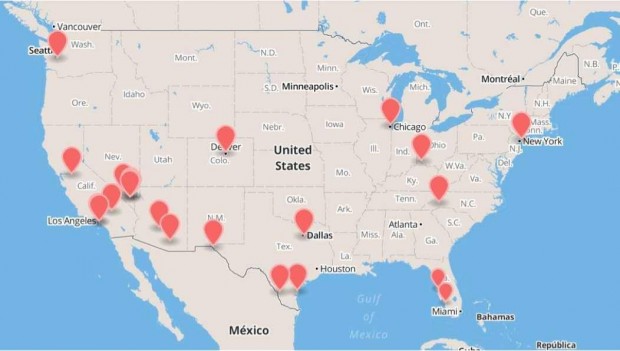
Here is the map from Goldsmith and his company showing where the “towers” they located are:
This map from ESD America shows where its special phone picked up on “fake” tower pings. But the towers aren’t physical structures — they are devices that mimic towers.
This map from ESD America shows where its special phone picked up on “fake” tower pings. But the towers aren’t physical structures — they are devices that mimic towers.
But again, they’re not necessarily physical towers.
To be fair, the second site to pick up the “17 fake towers” story did eventually add a note at the top of its story admitting the confusion:
There have been many comments to this story from people who are assuming that these ‘towers’ are physical installations. There’s no reason to assume this is the case: it’s far likelier that they are mobile installations of the kind used not only by law enforcement and government agencies, but also by scammers and other criminals.
But the damage seemed to already be done when the original story took off.
Now you have a more complete picture. The use of such technology is still concerning and worth debate, but at least you know that some mysterious construction group isn’t necessarily erecting actual towers in the dead of night and disguising them. Instead, it seems more likely that law enforcement and other government agencies are doing it in a much more covert and frankly easy way with small device and laptop.
And that’s probably more scary.